Mathematical Machine Readable Authentication Protocols for Network Security
DOI:
https://doi.org/10.31033/abjar.2.2.2Keywords:
mathematics, network security, machineAbstract
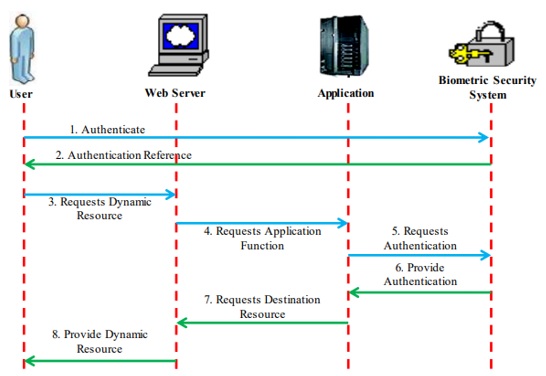
Since the International Civil Aviation Organization created standards that allow passports to store biometric identification, electronic passports have been widely and quickly embraced throughout the world. The use of biometrics for identification has the potential to improve people's quality of life and make the world a safer place to live in. By more precisely identifying a person, biometric passports are meant to stop travelers from entering a nation illegally and to reduce the use of fake documents. This article examines the biometric e-passport design for the face, fingerprint, palmprint, and iris. This article focuses on the personal security and privacy of e-passport holders, as well as the actual security benefits that governments have gained from the use of face, fingerprint, palmprint, and iris recognition technology in e-passports. Researchers looked at the facial fingerprint, palmprint, and iris biometrics now utilized with e-passports as well as the key cryptographic elements and supporting procedures. The report also offers a security evaluation of the e-passport's use of face fingerprint, palmprint, and iris biometrics, which are meant to increase security by safeguarding the ePassport holder's biometric data.
Downloads
References
A.K. Jian. (1999). Biometrics personal identification in networked society. Technical Report.
C. Hesher. (2003). A novel method for face recognition using range images. in: 7th International Symposium on Signal Processing and Its Application.
Home Affairs Justice. (2006). EU standard specifications for security features and biometrics in passports and travel documents. Technical Report, European Union.
ICAO. (2006). Machine readable travel documents. ICAO.
Klugler, D. (2005). Advance security mechanisms for machine readable travel documents. Technical Report.
Downloads
Published
How to Cite
Issue
Section
ARK
License
Copyright (c) 2023 R.M.L.S. Chandrarathna

This work is licensed under a Creative Commons Attribution 4.0 International License.
Research Articles in 'Applied Science and Biotechnology Journal for Advanced Research' are Open Access articles published under the Creative Commons CC BY License Creative Commons Attribution 4.0 International License http://creativecommons.org/licenses/by/4.0/. This license allows you to share – copy and redistribute the material in any medium or format. Adapt – remix, transform, and build upon the material for any purpose, even commercially.










