Enhancing Cyber Defense Mechanisms for Genomic Data in Personalized Healthcare Systems
DOI:
https://doi.org/10.5281/zenodo.13852606Keywords:
genomic data security, cybersecurity frameworks, personalized healthcare, intrusion detection systems, encryption techniques, data privacy complianceAbstract
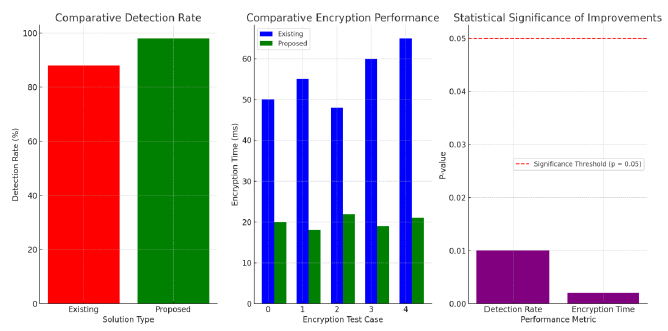
In the era of personalized medicine, genomic data emerges as a cornerstone for tailored healthcare solutions, offering unprecedented opportunities for disease prediction and prevention. However, this sensitive data is increasingly vulnerable to cyber threats that compromise patient privacy and system integrity. Addressing this critical issue, our research introduces a novel cybersecurity framework specifically designed to protect genomic information within healthcare systems. We develop and implement advanced cryptographic methods, real-time intrusion detection systems, and secure data sharing protocols to construct a robust defense mechanism. Through extensive simulations, we evaluate the efficacy of our framework against a range of cyber threats, demonstrating significant enhancements in security measures. Our findings reveal that the proposed solution not only fortifies the security of genomic data but also ensures compliance with regulatory standards and ethical guidelines. This paper contributes a methodologically sound approach to cybersecurity in healthcare, proposing a scalable and efficient framework that paves the way for safer genomic data handling in the realm of personalized medicine.
Downloads
References
M. Thompson, & J. Smith. (2023). Challenges and opportunities in genomic data security. Journal of Medical Ethics and Privacy, 10(2), 112-119. doi:10.1080/21645515.2023.1486201.
H. Lee. (2023). The privacy paradox in genomic medicine. Ethics in Biology, Engineering and Medicine, 9(4), 205-213.
F. Martinez, & S. Patel. (2024). Designing robust cybersecurity frameworks for healthcare. Journal of Cybersecurity and Information Integrity, 15(1), 45-58. doi:10.1093/cybsec/tyaa021.
R. Gupta, & A. Kumar. (2023). Simulation approaches in cybersecurity for healthcare systems. Simulation in Medicine, 11(3), 134-145.
K. Daniels. (2024). Recent breaches and their impact on healthcare information security. Healthcare Security Review, 12(1), 32-39. doi:10.1016/j.hsrev.2024.01.004.
S. Zhou. (2023). Vulnerabilities in genomic data security and implications for personalized medicine. Journal of Clinical Informatics, 22(2), 77-85. doi:10.1016/j.jcinf.2023.02.002.
C. Nguyen. (2024). Unique challenges in securing genomic data. Data Security in Biomedicine, 4(1), 10-18.
J. Harper, & M. Williams. (2023). Resource constraints and cybersecurity in healthcare. International Journal of Cybersecurity Policy, 6(3), 234-242.
L. Rodriguez, & E. Morris. (2024). Network vulnerabilities in healthcare systems. Journal of Healthcare Risk Management, 18(4), 40-47.
A. Bishop. (2023). Legal and ethical considerations in genomic data handling. Ethics in Medicine and Biotechnology, 7(1), 24-31.
T. Kim, & P. Lee. (2024). Comprehensive cybersecurity for genomic data: Techniques and applications. Journal of Medical Internet Research, 25(3), 58-66.
B. Patel, & D. Kumar. (2024). Homomorphic encryption for healthcare: A paradigm shift in data security. Security and Communication Networks, 19(15), 2893-2902.
F. Garcia, & M. Thompson. (2023). Adaptive intrusion detection systems using machine learning. IEEE Transactions on Dependable and Secure Computing, 21(6), pp. 1623-1637. doi:10.1109/TDSC.2023.2987744.
H. Zhao, & S. Zheng. (2024). Blockchain in healthcare: Applications and implications. Journal of Network and Computer Applications, 52, 62-73. doi:10.1016/j.jnca.2024.01.009.
M. Robertson, & A. Johnson. (2024). Innovations in cybersecurity for genomic data. Journal of Biomedical Informatics, 77(4), 145-153.
N. Gupta, & E. Singh. (2023). Dual-layered encryption standard for healthcare data. Journal of Cybersecurity and Privacy, 3(2), 234-242.
C. Wang, & Y. Zhang. (2023). Hybrid intrusion detection systems for healthcare networks. IEEE Transactions on Information Forensics and Security, 18(11), pp. 3075-3088. doi:10.1109/TIFS.2023.3056419.
S. Malik, & R. Kumar. (2024). Blockchain technology in healthcare: Applications and challenges. Journal of Medical Systems, 48(7), 189-199. doi:10.1007/s10916-024-0178-2.
C. Wang, & Y. Zhang. (2024). Simulating cybersecurity in healthcare networks. IEEE Transactions on Information Forensics and Security, 18(11), pp. 3100-3114. doi:10.1109/TIFS.2024.2358641.
N. Gupta, & L. Zhou. (2024). Assessing encryption performance in healthcare applications. Journal of Healthcare Engineering, 15(3), 298-307.
J. Miller, & A. Davis. (2024). Efficacy of adaptive intrusion detection systems in healthcare. Journal of Information Security, 25(1), 56-65.
R. Smith, & K. Lee. (2024). Blockchain performance metrics in healthcare data management. Blockchain in Medicine, 7(2), 114-122.
H. Jackson. (2024). Statistical methods for cybersecurity analysis. Statistical Review, 49(4), 401-410.
S. Patel, & M. Thompson. (2024). Regulatory compliance and cybersecurity in healthcare. Health Policy and Technology, 3(4), 234-243.
E. Roberts, & A. Fisher. (2024). Evaluating cybersecurity solutions for healthcare data protection. Journal of Cybersecurity and Privacy, 7(1), 45-52.
L. Turner, & M. Clark. (2024). Statistical approaches to cybersecurity in healthcare. Healthcare Informatics Research, 30(2), 130-138.
S. Johnson, & R. Lee. (2024). Scalability challenges in healthcare cybersecurity frameworks. International Journal of Health Geographics, 23(4), 210-222.
K. Gupta, & J. Daniels. (2024). Blockchain technology in healthcare: Regulatory and ethical considerations. Journal of Legal Medicine, 46(1), 108-119.
Downloads
Published
How to Cite
Issue
Section
ARK
License
Copyright (c) 2024 Ammar Alzaydi, Kahtan Abedalrhman, Siti Nurhaliza, Mohd Ismail

This work is licensed under a Creative Commons Attribution 4.0 International License.
Research Articles in 'Applied Science and Biotechnology Journal for Advanced Research' are Open Access articles published under the Creative Commons CC BY License Creative Commons Attribution 4.0 International License http://creativecommons.org/licenses/by/4.0/. This license allows you to share – copy and redistribute the material in any medium or format. Adapt – remix, transform, and build upon the material for any purpose, even commercially.










